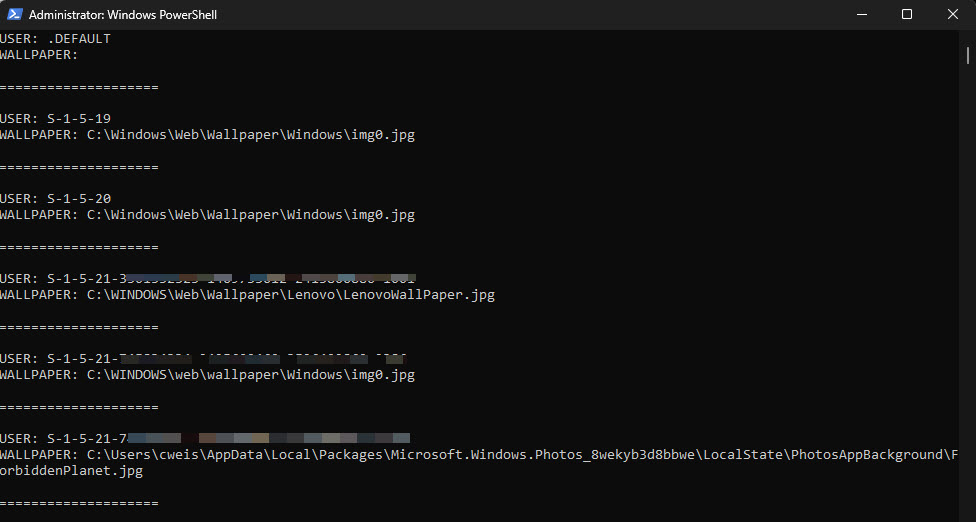
This is a small example I put together on how to quickly loop through each user SID in HKEY_USERS and find the value that shows what the wallpaper is set to for each user. This little script is a decent reference to use for finding (And with a little modification, setting) registry value(s) in the HKEY_USERS section.
<#
.DESCRIPTION
Example to show how you can go through each user branch in registry
HKEY_USERS and retrieve the wallpaper file path key.
#>
$hkUsers = [Microsoft.Win32.RegistryKey]::OpenRemoteBaseKey('USERS', $env:COMPUTERNAME)
$hkUsersSubkeys = $hkUsers.GetSubKeyNames()
$hkUsersSubkeys | % {
$hkeyuserpath = "$_\Control Panel\Desktop"
$hkeyuserpath = "REGISTRY::HKEY_USERS\$hkeyuserpath"
Write-Host "`nUSER: $_"
$wallpaperfile = (Get-ItemProperty -Path $hkeyuserpath -ErrorAction SilentlyContinue).Wallpaper
Write-Host "WALLPAPER: $wallpaperfile`n`n===================="
}